1. Introduction
- Risk Management
- Who Are You, and Why Are You Here?
- Finding a Solution
2. Problem Definition
- What Needs Protecting?
- Who is Allowed Where?
3. Methods of Identification
- Reliability vs. Cost
- Combining Methods to Increase Reliability
- Security System Management
4. Access Control
- What You Have
- What You Know
- Who You Are
5. Other Security Systems Elements
- Building Design
- Piggybacking and Tailgating: Mantraps
- Camera Surveillance
- Security Guards
- Sensors and Alarms
- Visitors
6. The Human Element
- People: The Weakest Link
- People: The Strongest Backup
7. Site Design
- Layers
- Components
- Tactics
8. Controlling Site Access
- Entry Control Facility
- Zones of an Entry Control Facility
- Utilities and Automatition
9. Chosing the Right Solution
- Risk Tolerance vs. Cost
- Security System Design Considerations
- Building Security Design Considerations
|
 |
Site Design - 1 - Layers
Defending the Perimeter - 1st Layer:
Outermost perimeter is line of demarcation.
- Crossing the boundary establishes intent - marks an aggressor.
- It is the first opportunity to provide detection.
- Usually provides minimal delay.
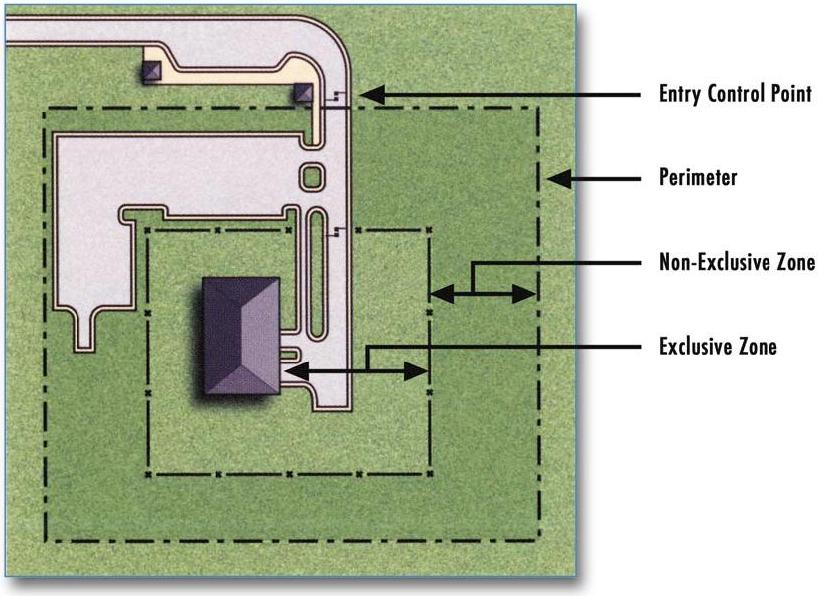
Exclusion Zone - 2nd Layer:
Defined inner perimeter or open space.
- Obstruction free or clear zone.
- Allows detection of aggressors or threats.
- Supports sensor based detection.
Traveling across intermediate space is vulnerability for aggressor and
provides delay.
Building Exterior - 3rd Layer:
Depending on level of public access, building exterior may be significant
layer of the protective system. It defines the end of site security. The remaining layers are defined within the building as appropriate for the assets within.
To receive your Physical Vulnerability Assessment, please submit your payment of $999.00
B E T T E R: Please submit your payment of $1999.00 for a complete Physical Vulnerability Assessment or Design covering a single location.
|


