Tools: Metasploit
Have you ever wondered how you can execute the ever so vague "arbitrary code" that Microsoft lists in its vulnerability descriptions to see if your systems are really vulnerable? Maybe you've wanted to dig deeper into the higher-level flaws found by vulnerability assessment tools such as Nessus and QualysGuard? Perhaps you're in the business of ethical hacking and performing penetration tests against your own (or your customer's) computer systems? If any of these apply to you, there's a powerful security testing tool that you can't miss.
I'm talking about the Metasploit Framework. It's not new -- in fact, it has been around for a couple of years. However, it has recently started to pick up traction and command attention from information security professionals and software developers alike. Many of us are realizing that Metasploit is an indispensable tool that provides a solution to some vexing information security issues from exploit conception to execution.
Interestingly, the Metasploit Framework started out as a portable network game (don't ask me). Recently, it has evolved into a formidable tool for performing security vulnerability research, developing exploit code and (the really cool part) automating the process of exploiting vulnerable software. Its well-written documentation is only 34 pages long -- quite surprising for a tool of this caliber. Most white hat security professionals don't have the patience, time and often the expertise to code their own exploits. In addition, many of us want to take our testing to the next level or streamline our methodologies to make things easier. Every now and then developers and security experts come together and provide a great solution to fill in the gaps. The Metasploit Framework does just that.
Metasploit is similar to the commercial penetration testing products -- CANVAS by Immunity Inc. and CORE IMPACT by Core Security Technology -- with one big difference: It's open source, so it's free! It runs on Windows (via a scaled-down version of Cygwin), Linux, BSD and OS X. Its main interface is called msfconsole (shown in Figure 1).
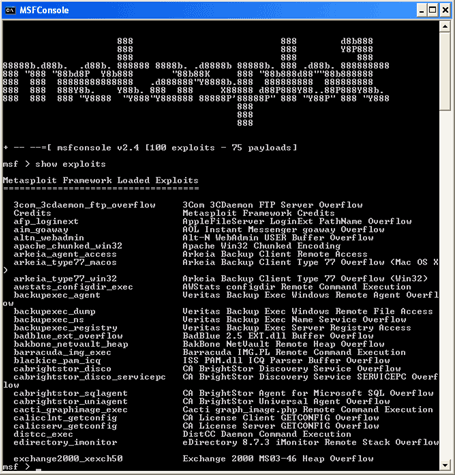
Figure 1 – The Metasploit Framework console interface
Msfconsole is where you select and customize various exploits and payloads based on the system you're testing. Metasploit also has a command line interface (msfcli) and even a built-in Web server (msfweb) for those who want to use the tool via a happy-clicky GUI Web browser. Based on where your test system is located, you can run exploits either inside or outside a firewall, which can be very beneficial. Adding to its testing flexibility, Metasploit allows you to send various attack payloads (code that runs on the exploited system) depending on the specific exploits you run.
Currently, a half-dozen or so exploits in Metasploit exploit Windows-specific vulnerabilities. However, there are many others that apply to software that runs on Windows such as Exchange, SQL Server, IIS, BackupExec, BlackICE and AOL Instant Messenger -- quite likely software that's running on your network. Metasploit isn't just for Windows shops either -- there are exploits for practically every popular operating system platform.
Metasploit is a powerful tool that can be abused if it's in the wrong hands -- but that's an age-old problem that we have little control over in a free society. If you use it in an ethical fashion, the way it was intended, you can prove that idle vulnerabilities are indeed exploitable. And, there's hardly any better way to get the attention of management or those administering the system than a problem that really does exist. It's hard for anyone to argue against hard evidence (via a few telling screen captures) showing how easily a system can be owned or taken down.
This is just the tip of the Metasploit Framework iceberg from a penetration perspective. In a future tip, I'll outline how you can use its testing capabilities in some real-world scenarios.